ぷららのTransix DS-Lite(IPv4 over IPv6)からのアクセスがヨーロッパ圏からのアクセス?
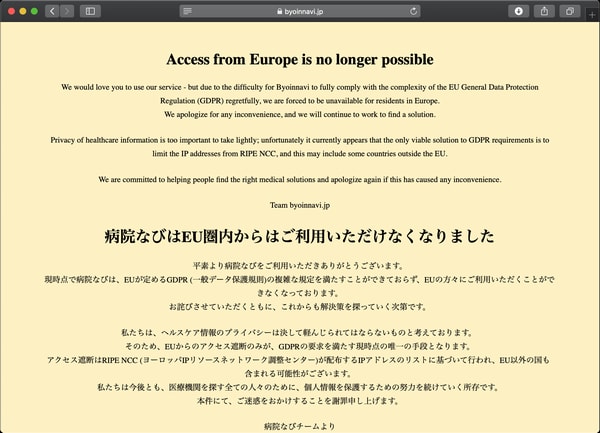
transix DS-Liteは、日本国内にあるかと。。。
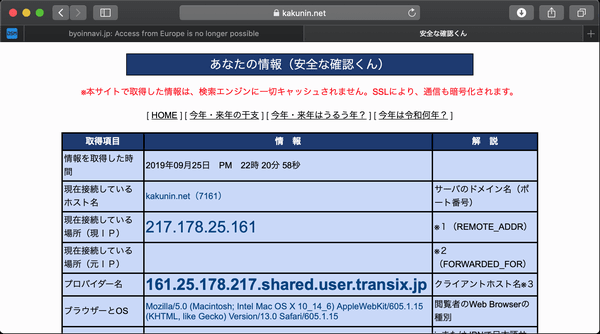
IPアドレスで判断する愚。。。。
また、ぷららのサポートに問い合わせるのかな。。。。。

transix DS-Liteは、日本国内にあるかと。。。

IPアドレスで判断する愚。。。。
また、ぷららのサポートに問い合わせるのかな。。。。。


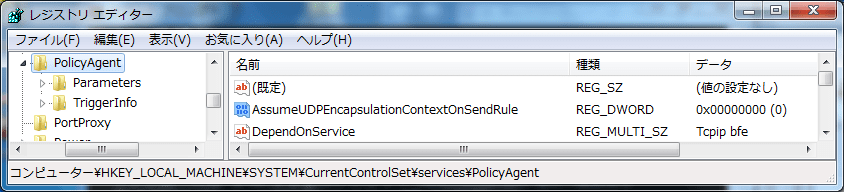




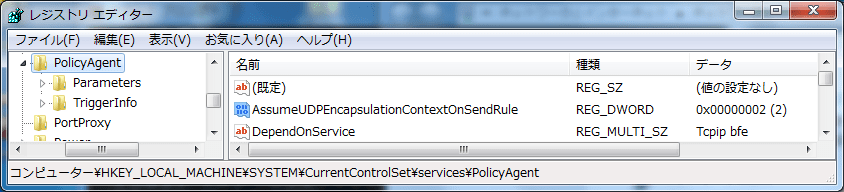




AES-128-CBC
<key>ChildSecurityAssociationParameters</key>
<dict>
<key>DiffieHellmanGroup</key>
<integer>14</integer>
<key>EncryptionAlgorithm</key>
<string>AES-128</string>
<key>IntegrityAlgorithm</key>
<string>SHA1-96</string>
<key>LifeTimeInMinutes</key>
<integer>1440</integer>
</dict>
AES-256-CBC
<key>ChildSecurityAssociationParameters</key>
<dict>
<key>DiffieHellmanGroup</key>
<integer>14</integer>
<key>EncryptionAlgorithm</key>
<string>AES-256</string>
<key>IntegrityAlgorithm</key>
<string>SHA2-256</string>
<key>LifeTimeInMinutes</key>
<integer>1440</integer>
</dict>
AES-128-GCM
<key>ChildSecurityAssociationParameters</key>
<dict>
<key>DiffieHellmanGroup</key>
<integer>14</integer>
<key>EncryptionAlgorithm</key>
<string>AES-128-GCM</string>
<key>IntegrityAlgorithm</key>
<string>SHA1-96</string>
<key>LifeTimeInMinutes</key>
<integer>1440</integer>
</dict>
AES-256-GCM
<key>ChildSecurityAssociationParameters</key>
<dict>
<key>DiffieHellmanGroup</key>
<integer>14</integer>
<key>EncryptionAlgorithm</key>
<string>AES-256-GCM</string>
<key>IntegrityAlgorithm</key>
<string>SHA2-256</string>
<key>LifeTimeInMinutes</key>
<integer>1440</integer>
</dict>
/etc/ipsec.conf
conn %default
keyexchange=ikev2
#for Windows10 IKEv2 VPN
ike=aes256-sha256-modp1024
#for GCM testing
esp=aes128gcm16-sha, aes256gcm16-sha256
auto=add
left=%any
leftauth=pubkey
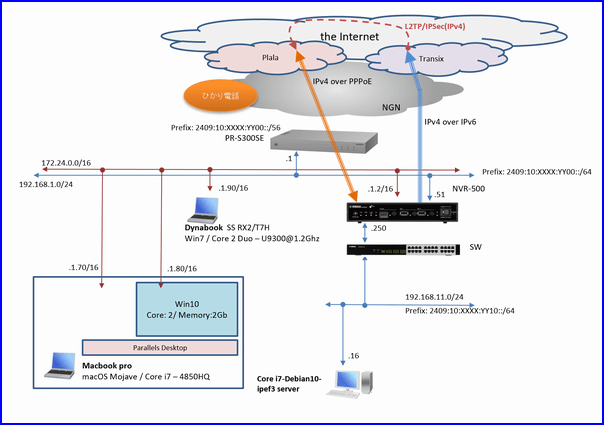
leftsubnet=192.168.0.0/20,2409:10:XXXX:YY00::/56,2404:1a8::/32
#for iOS VPN apli
leftsendcert=always
leftcert=debian10-pub.pem
leftid=@vpn.AAAAAAAA.mydns.jp
right=%any
rightsourceip=192.168.15.0/24,2409:10:XXXX:YY30::15:0/120
rightdns=192.168.11.250,2409:10:XXXX:YY20::11:250root@debian10:~$ lscpu
Architecture: x86_64
CPU op-mode(s): 32-bit, 64-bit
Byte Order: Little Endian
Address sizes: 36 bits physical, 48 bits virtual
CPU(s): 8
On-line CPU(s) list: 0-7
Thread(s) per core: 2
Core(s) per socket: 4
Socket(s): 1
NUMA node(s): 1
Vendor ID: GenuineIntel
CPU family: 6
Model: 42
Model name: Intel(R) Core(TM) i7-2600 CPU @ 3.40GHz
Stepping: 7
CPU MHz: 1596.243
CPU max MHz: 3800.0000
CPU min MHz: 1600.0000
BogoMIPS: 6784.69
Virtualization: VT-x
L1d cache: 32K
L1i cache: 32K
L2 cache: 256K
L3 cache: 8192K
NUMA node0 CPU(s): 0-7
Flags: fpu vme de pse tsc msr pae mce cx8 apic sep mtrr pge mca cmov pat pse36 clflush dts acpi mmx fxsr sse sse2 ss ht tm pbe syscall nx rdtscp lm constant_tsc arch_perfmon pebs bts rep_good nopl xtopology nonstop_tsc cpuid aperfmperf pni pclmulqdq dtes64 monitor ds_cpl vmx smx est tm2 ssse3 cx16 xtpr pdcm pcid sse4_1 sse4_2 x2apic popcnt tsc_deadline_timer aes xsave avx lahf_lm epb pti tpr_shadow vnmi flexpriority ept vpid xsaveopt dtherm ida arat pln pts
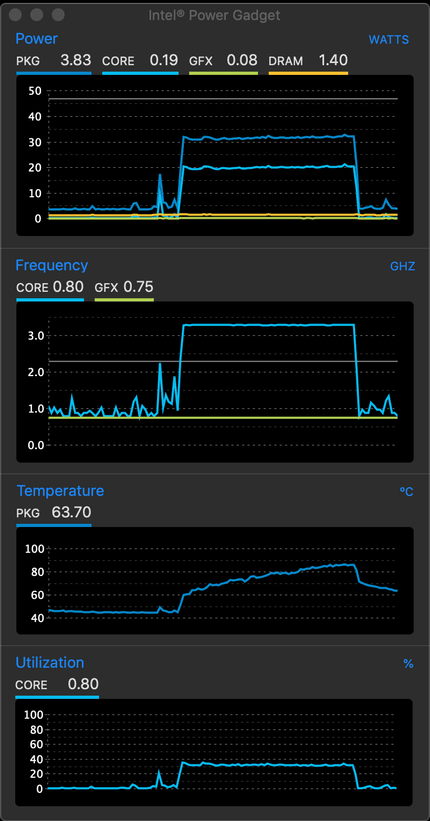
openssl speed aes-256-cbc
OpenSSL 1.1.1c 28 May 2019
built on: Thu May 30 15:27:48 2019 UTC
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
aes-256 cbc 84293.98k 89436.65k 90589.10k 91029.16k 91187.88k 91247.96k
openssl speed -evp aes-256-cbc
The 'numbers' are in 1000s of bytes per second processed.
type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes 16384 bytes
aes-256-cbc 393369.35k 491012.78k 523522.90k 532274.52k 534899.37k 535183.36k












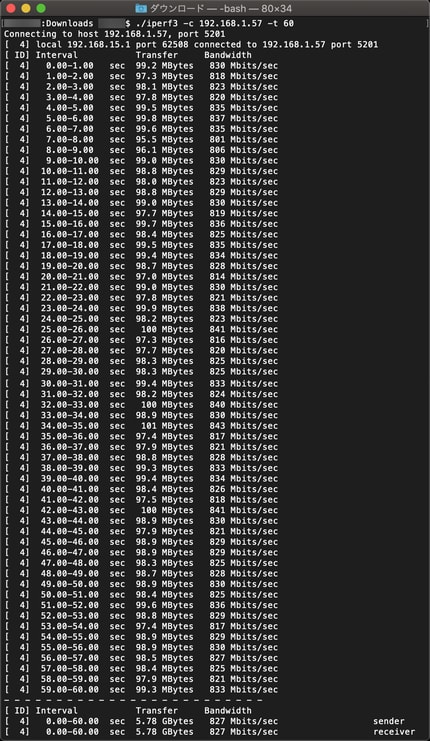
AES128-CBC 825Mbps AES256-CBC 682Mbps AES128GCM16 878Mbps AES256GCM16 824Mbps


/etc/ipsec.conf
config setup
# strictcrlpolicy=yes
# uniqueids = no
# charondebug="cfg 2,ike 2,esp 2"
conn %default
keyexchange=ikev2
#for Windows10 IKEv2 VPN
ike=aes256-sha256-modp1024
# esp=aes128-sha!
auto=add
left=%any
leftauth=pubkey
leftsubnet=192.168.0.0/20,2409:10:XXXX:YY00::/56,2404:1a8::/32
#for iOS VPN apli
leftsendcert=always
leftcert=debian10-pub.pem
leftid=@vpn.AAAAAAAA.mydns.jp
right=%any
rightsourceip=192.168.15.0/24,2409:10:XXXX:YY30::15:0/120
rightdns=192.168.11.250,2409:10:XXXX:YY10::11:250
conn eap-id-passwd
rightauth=eap-mschapv2
eap_identity=%any/etc/ipse.secrets
: RSA debian10-key.pem "key password"
user1 : EAP "user password"
/etc/strongswan.conf
charon {
load_modular = yes
plugins {
include strongswan.d/charon/*.conf
#for iOS/OSX IKEv2 VPN apli
attr {
25 = familyname,flets-east.jp
}
}
}
include strongswan.d/*.conf